Terrifying Grindr security flaw leaks people’s exact locations

A phone displays the logo of gay hook-up app Grindr (Getty)
A massive security flaw allowing people to generate maps of people’s precise locations on Grindr has been exposed.
Queer Europe posted an exposé of the app’s flaws, revealing that freely-available third-party tools have been created to take advantage of Grindr’s vulnerabilities.

Grindr (Leon Neal/Getty)
Although Grindr usually only shows the distance between two users who have locations switched on, according to Queer Europe, it is possible for rogue users to take measurements from different locations and triangulate the location of other people on the app.
This process was achieved by one third-party tool titled F**kr, which took advantage of location spoofing to send a vast number of requests to Grindr’s servers, using the data to calculate “within seconds” the position of every nearby user, down to the individual house or business in some cases.
The tool also pulled data from users’ profiles on the app, detailing people’s names, preferred sexual positions, HIV status and profile photos alongside their exact geographic location.
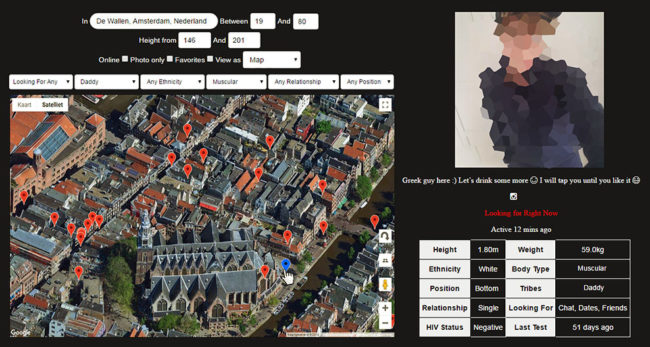
In addition to facilitating the mapping of all users, security weaknesses also allow users to search for the current location of a specific person on Grindr without their knowledge, it’s claimed.
Queer Europe explains: “As an experiment, a friend allowed me to track him during a Saturday night out. While sitting behind my laptop, I could see in which restaurants he was eating, in which cafes he was drinking, and in which nightclubs he was dancing. I could also see that he went to the gay sauna at 1 AM and then slept at a stranger’s house at 3 AM.
“By making it so easy to track individuals with precision, Grindr makes its users extremely vulnerable to harassment and stalking.”
Applications designed to locate Grindr users are publicly available online, and give anyone access to a virtual map on which you can travel from city to city, and from country to country, while seeing the exact location of cruising men that share their distance online. pic.twitter.com/0IumD6laAE
— Queer Europe ️ (@QueerEurope) September 13, 2018
Grindr disables location features in a number of countries where LGBT+ people face persecution, but the blog adds that the vulnerability could be exploited in countries with homophobic records, including Algeria, Turkey, Belarus, Ethiopia, Qatar, United Arab Emirates, Oman, Azerbaijan, China, Malaysia and Indonesia.
The specified third-party tool was posted for free use on GitHub. It has now been removed following a copyright takedown notice, but its functions can be replicated.
The alleged flaws raise concerns that the same vulnerabilities could be exploited by governments to collate mass data on Grindr users, for blackmail or direct persecution.
Queer Europe said: “Grindr should be more explicit about the ways in which information shared by users can be obtained and processed by third parties.”
The website also said it was “crucial” for Grindr to warn users about these purported dangers.
Grindr has faced strong criticism in the past over a number of security flaws, which have allowed people to track people’s locations and access the list of users who blocked them.
The company was also forced to apologise when it emerged it was handing over user data including HIV status to third parties.
Grindr president Scott Chen told BuzzFeed that geolocation is “core to our platform and user experience,” but said the company “will continue trying to evolve and improve our platform.”

